
Cybersecurity is a demanding career path for cybersecurity analysts. According to Cybersecurity progress, the number of unfilled cybersecurity jobs increased by 80 percent in the world of technology, from one million in 2018 to 3.5 million in 2022. The cybersecurity skills gap is narrowing for the first time in a decade. In the future, we expect the demand for Cybersecurity grows. Moreover, cybersecurity analysts paid more than 2 to 3 lakhs per year.
Further, cybersecurity analysts have worldwide job opportunities for freshers and professionals. More than 90,000 people work in cybersecurity in the United States, with roughly 460,000 positions still open. The job environment in the United States reflects a global scarcity of candidates with cybersecurity certifications. So, candidates with the cybersecurity certificate have access to wider opportunities. So, you can join Cyber Security Course In Bangalore to have a profound understanding of cybersecurity techniques which helps to have exposure to wider opportunities.
In this blog, we shall discuss why Cybersecurity is a demanding career, ARP poisoning attack, ARP spoofing attack, arp cache poisoning, and what is arp spoofing.
Why Cybersecurity is a Demanding Career
A cybersecurity analyst defends a company against cybercrime and actively creates processes for responding to and countering cyberattacks. Cybersecurity analysts defend a firm's infrastructure, such as computer networks and physical devices, against cybercriminals and hackers looking to harm or steal critical data.
Who is a Cybersecurity Analyst
A cybersecurity analyst is a qualified cyber professional focusing on network security and IT system security. The cybersecurity analyst is well-versed in hacks, malware, and cybercriminal behaviour and works diligently to anticipate and avoid these attacks. Typically, the Analyst has a bachelor's degree in Cybersecurity or a similar discipline.
Companies that Hire Cybersecurity Analyst
Many top IT and non-IT companies hire cybersecurity analysts. The hire companies are StrongBox IT, Ford Motor Company, Accenture, Wipro Limited, Wolters Kluwer India Private Limited, Harman International NTRO National Technical Research Organisation, Astra Security, etc.
In all these companies, you will obtain common roles like Junior Security Analyst, Cyber Security Analyst, Cyber Security Risk Analyst, Security Operations Analyst, Cyber Security Contract Analyst, Senior Security Analyst, Information Security Analyst, - Automotive Cybersecurity Analyst, Cloud Security Analyst, Automotive Cybersecurity Compliance Analyst, etc.
Moreover, there are plenty of job opportunities for freshers and professionals to begin their careers in the cybersecurity industry.
As the demand for Cybersecurity increases, businesses are focusing more on hiring workers with the necessary skills and technical expertise. So, completing a cybersecurity course would help sustain you in the security industry and have the chance to work in companies worldwide.
FITA Academy is the best institute for the Ethical Hacking Course in Chennai. Those who intend to begin their career as ethical hackers can join and explore their careers in the IT sector.
Before discussing the arp poisoning attack, arp spoofing attack, arp cache poisoning, what is arp spoofing; we shall discuss Cybersecurity Skills.
Cybersecurity Skills
The risk and threats of cyber-attacks have grown in tandem with technological advancements. Due to the increasing severity and frequency of cyber assaults, bridging the cybersecurity skill would help you have a broader scope.
Suppose you're interested in learning about cybersecurity and pursuing a career in it. In that case, you should have these basic skills such as knowledge of Hacking, Cloud Security, Computer Forensics Skills, Blockchain Security, Artificial Intelligence, Programming Skills(Java, PHP, C, or C++), IoT Security, and Communication Skills, and Problem-Solving Skills.
We shall discuss hacking knowledge in the essential and profound understanding of arp poisoning attack and arp spoofing attack.
Why Hacking Knowledge is Essential
Hacking can be a genuine professional career path. Cybersecurity is a rapidly growing field with a wide range of job options. Many companies hire ethical hackers to evaluate their security systems to ensure they're not exposed to black hat hackers. So, to have comprehensive understanding, you can join Ethical Hacking Course In Chennai and impart the 5 Phases of Ethical Hacking, Types of Footprinting, Enumeration Countermeasures, etc.
As mentioned above, hacking knowledge is essential; the hacking techniques and tools aid in testing vulnerability in the system and protecting the system's data from a malicious hacker. As a result, many large corporations, such as Google, Yahoo, Instagram, Facebook, and Uber, employ hackers.
Ethical hacking is used to protect sensitive information from malicious hackers. It protects your computer from exploitation by those looking to take advantage of a weakness. A firm or organization can use ethical hacking to identify security vulnerabilities and dangers.
Now, we shall discuss tools used to hack the system types of hackers.
Hacking Tools
Hacking is the process of identifying a network or system to which you are not intended to have access. 'Hacking' is a phrase that can be used to describe a wide range of behaviors, in which hacking tools are utilized by both legal and illegal hackers.
For example, suppose we are attempting to connect to an email account to which we do not have access. In such a case, hacking tools are required, so hackers utilise tools such as Sboxr, IKECrack, Rainbow Crack, WebInspect, LiveAction, Aircrack, Traceroute NG, etc.
Types of Ethical Hackers
-
Black Hat Hackers- Because they hack into a system, steal data, conduct fraud, or utilize it for personal gain, black hat hackers are referred to as criminals.
-
White Hat Hackers- White hat hackers (also known as white hats) use the same methods and tools as black hat hackers to break into systems. Unlike black hat hackers, Whitehat hackers only hack systems that have permitted them. Ethical hackers, penetration testers, and pen testers are used to describe white hats.
-
Grey Hat Hackers- Grey hat hackers walk between legal and unethical hacking. These individuals can break into any network, even if they lack the authority to assess its security.
To have in-depth understanding of ethical hacking concepts, you can join Ethical Hacking Course In Bangalore and equip with the necessary concepts such as Enumeration Techniques, Network Scanning Technique, Footprinting Tools and Countermeasures.
Now, we shall discuss password cracking and arp poisoning, arp poisoning attack, arp spoofing attack and types of hacking.
Types of Hacking
As we discussed before, hacking is the method of breaching the system to steal the organization's confidential data.
Phishing, Missing Security Patches, UI redress, Malware-Injection Devices, viruses, Cookie theft, Distributed Denial-of-service(DDoS), DNS spoofing, Cracking Password, Email hacking, and Social Engineering.
Ethical Hacking - ARP Poisoning attack
ARP (Address Resolution Mechanism) is a protocol that allows computers to resolve Internet Protocol addresses to Media Access Control address addresses. To determine other devices' Media Access Control address addresses, all network components that require network connectivity broadcast ARP queries in the system. Address Resolution Mechanism Poisoning is a sort of Address Resolution Mechanism poisoning known as ARP Spoofing.
-
When one system needs to talk to another, it consults its Address Resolution Mechanism table.
-
The ARP request is broadcast over the network if the MAC address is not located in the table.
-
This IP address will be compared to the Media Access Control address of all machines on the network.
-
If one of the computers on the network recognizes this address, it will respond with its IP and MAC address to the Address Resolution Mechanism request.
-
The device will store the IP address in its arp table and communicate.
What is an ARP Spoofing attack?
Address Resolution Protocol is a type of hacking in which an illegal hacker sends the forged ARP (Address Resolution Protocol) messages over a LAN.
-
ARP spoofing creates a large number of fake ARP requests and responses to load the switch.
-
In networking, a switch is a high-speed device that captures data packets and routes them to their intended target on a local area network (LAN).
Poisoning occurs when an attacker assaults a target device's ARP cache with fake entries. Man-in-the-Middle access is used to poison the network through ARP poisoning.
What is MITM?
The Man-in-the-Middle attack is a type of active assault in which the attacker pretends to be the user by establishing a link between the victims and sending communications between them. In this situation, the victims believe they are communicating with one another, but the illegal actor actually controls the conversation.
An attack's purpose is to obtain private information such as usernames and passwords, bank details, and credit card information. Typical targets are obtained from financial apps, SaaS firms, e-commerce sites, and other websites that require signing in.
Cybercrime, unauthorized fund transfers, and illegal password changes could be feasible with information gathered during an attack.
A MITM attack is essentially the same as a postal accessing your financial statements, jotting down your account information, then resealing and bringing it to your door. In short, there is a third party who manages and controls the communication transfer between two parties. Some protocols, such as SSL, are designed to guard against such attacks.
ARP Poisoning − Exercise
We used BetterCAP to accomplish Address Resolution Protocol poisoning in a Local area network setting utilizing a VMware workstation with Kali Linux deployed and the Ettercap application to detect the local traffic in the Local area network.
The following tools are required for this exercise:
This assault can be carried out on both wired and wireless networks. This attack can be carried out on a Local area network. Now, we shall discuss the arp poisoning attack.
Step 1: Deploy the Vmware tools and the Kali Linux OS in
Step 2: Login to Kali Linux with the username and password "root, too."
Step 3: Verify that you are linked to a local LAN and check your IP address using the ifconfig command in the console.
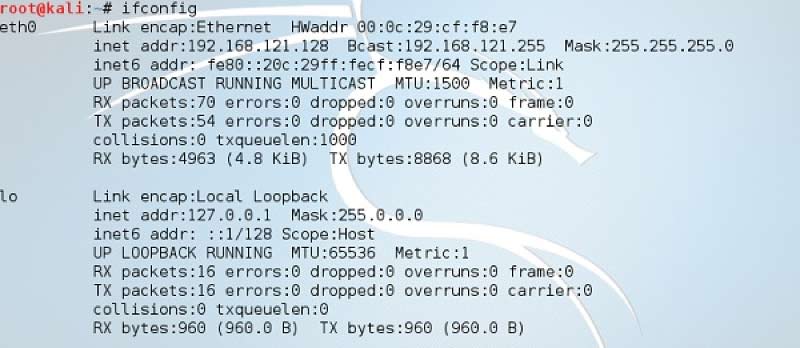
Step 4 − To begin the graphical version of Ettercap, open a terminal and enter "Ettercap –G."
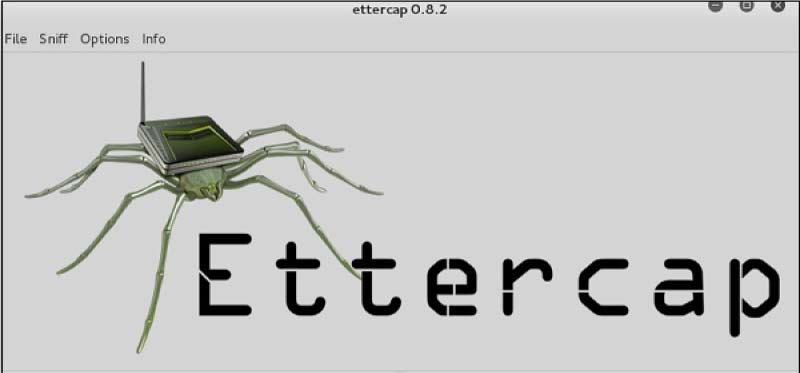
Step 5 −Select "unified sniffing" from the menu bar's "sniff" option, then click OK to choose the interface. We shall use "eth0," which stands for Ethernet connection.
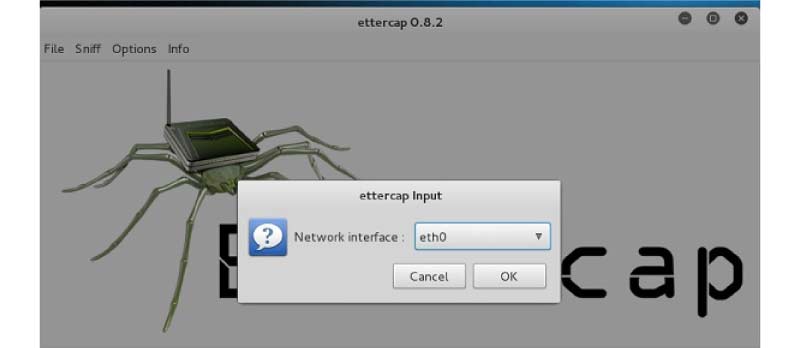
Step 6: Pick the "hosts" tab in the menu bar and then "search for hosts." It will begin searching the entire network for active hosts.
Step 7: Select "hosts list" from the "hosts" menu to examine the number of servers available in the network. The default route address is also included in this list. When choosing targets, we must be cautious.

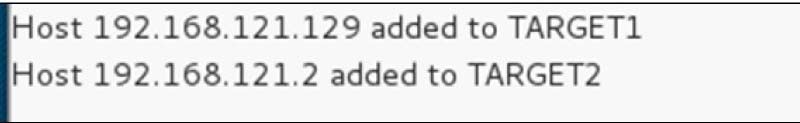
Step 8 − We must now select the objectives. The host computer will be our victim in MITM, and the pathway will be the network address used to forward traffic. The attacker can access the internet and inhale the packets in a MITM attack. As a result, "target 1" will be the victim, and "target 2" will be the router IP.
When "1" is given to the physical host in a VMware environment, the default gateway will always conclude with "2."
Step 9 − The destination, in this case, is "192.168.121.129," and the gateway is "192.168.121.2." As a result, we will make target 1 the victim and target 2 the gateway.
Step 10 − Now, go to "Man in the middle attack" and select "ARP poisoning." After that, select "Sniff network connection" from the drop-down menu and click OK.
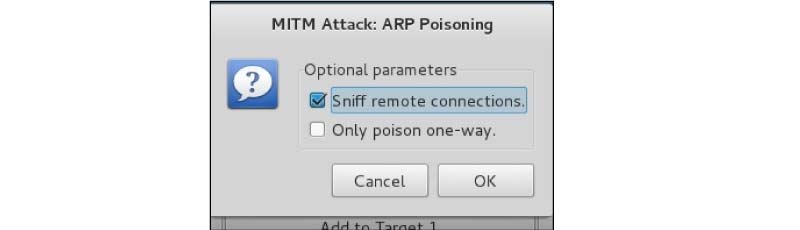
Step 11 − Select "start sniffing" from the "start" menu. This will cause ARP poisoning in the network, indicating that we have enabled "promiscuous mode" on our network card, allowing us to sniff local data.
With Ettercap, we've just authorized HTTP sniffing.
Step 12: Check the results to determine if our target logged onto any websites. In Ettercap's toolbar, you can view the results.
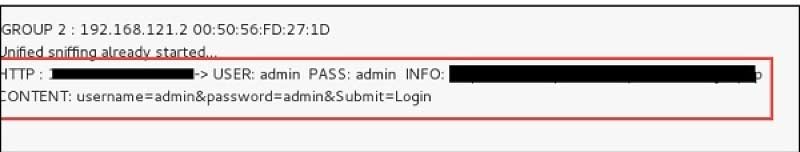
This is the process of sniffing. You must have realized how simple it is to obtain HTTP passwords simply by using ARP poisoning.
In the business, ARP poisoning can impose substantial losses. This is where ethical hackers are assigned to keep the networks secure.
Other attacks, such as Media Access Control flooding, MAMedia Access Control spoofing, DNS poisoning, Internet Control Message Protocol poisoning, and so on, can cause considerable network loss, just as ARP poisoning.
Now, you would have understood the password cracking and arp poisoning, arp poisoning attack, arp spoofing attack, arp cache poisoning, and what is arp spoofing. Moreover, we have also discussed what cybersecurity is, types of hacking tools, types of hackers, and types of hacking. So, to head your career in the cybersecurity industry, you can join a cybersecurity course. Moreover, you can take up an ethical hacking course to access wider opportunities. So, join Cyber Security Course in Chennai to have a comprehensive understanding of Networking, cybersecurity techniques, etc.